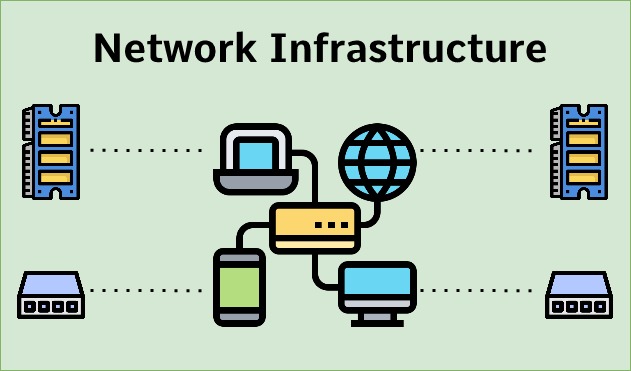
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
Network Infrastructure
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
- 🌐 Network Topologies
- 🖧 Networking Devices and Hardware
- 📶 Network Cabling and Transmission Media
- 🛡️ Network Security Fundamentals
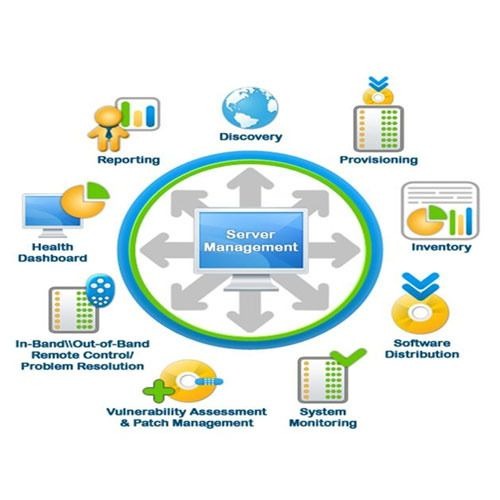
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration
Server Management
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
- 📁 File and Print Services
- 🛠️ Server Hardware and Architecture
- 🔒 User and Permission Management
- 📡 Network Configuration

Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security
Virtualization
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
- 🖥️ Virtualization Platforms Overview
- 📡 Networking in Virtual Environments
- 💾 Virtual Storage Management
- 🔒 Virtual Machine Security

Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
Data Storage
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
- 🧱 Storage Architectures
- 🌐 Storage Networking Protocols
- 🔒 Storage Security
- 📦 Backup and Recovery
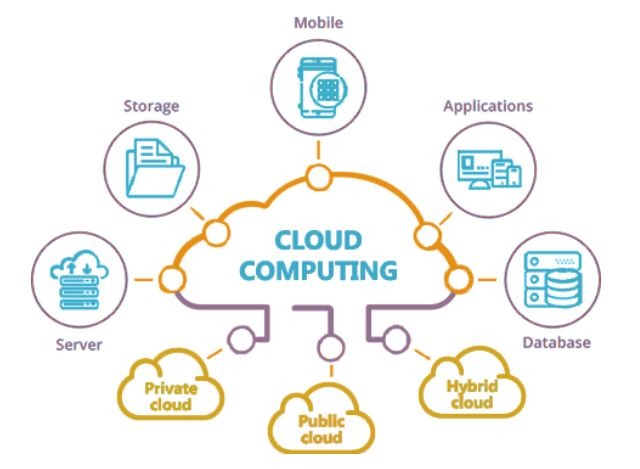
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components
Cloud Computing
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
- 🏛️ Cloud Service Models
- 🗃️ Cloud Deployment Models
- ☁️ Major Cloud Platforms Overview
- 🛠️ Cloud Infrastructure Components

Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption
Cybersecurity
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
- 🔐 Network Security
- 🛡️ System and Endpoint Security
- 👤 Identity and Access Management (IAM)
- 🔒 Data Security and Encryption

Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery
Disaster Recovery
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
- 📋 Developing a Disaster Recovery Plan
- 💽 Backup Strategies
- 🛠️ Technologies for Disaster Recovery
- ☁️ Cloud-Based Disaster Recovery

Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management
Linux Administration
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
- 📌 Introduction to Linux
- 💻 Linux Installation and Boot Process
- 🔧 Linux Command Line Basics
- 👥 User and Group Management