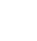How to Stay Motivated and Succeed in Online Courses
Discover the must-have books of the season, from thrilling mysteries to inspiring biographies.
Loading...
Gain expertise with access to over 24,000 video courses.
Learn from courses taught by industry experts.
Learn anytime, anywhere with unlimited access on any device.







Education is one of the most essential and valuable assets that an individual can possess, It plays a pivotal role in shaping
The Flexible Classes feature allows students to customize their learning schedule
All trainers hold relevant certifications and advanced degrees, guaranteeing that you are learning from qualified experts
Prepare for job interviews with mock interview sessions, feedback, and tips on how to present yourself confidently
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
Definition and components of network infrastructure.Star, Ring, Bus, Mesh, and Hybrid.Routers, switches, hubs, bridges, repeaters
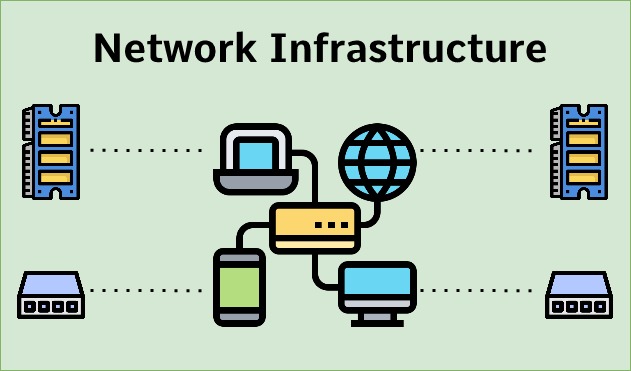
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)
What is a server? Role and types.Server components: CPU, RAM, storage, NICs.Installing Windows Server/Linux (Ubuntu, CentOS)

Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM
Benefits: cost efficiency, flexibility, resource optimization.Popular platforms: VMware, Hyper-V, VirtualBox, KVM

Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
Importance in IT infrastructure.Primary vs. Secondary storage.Direct Attached Storage (DAS)
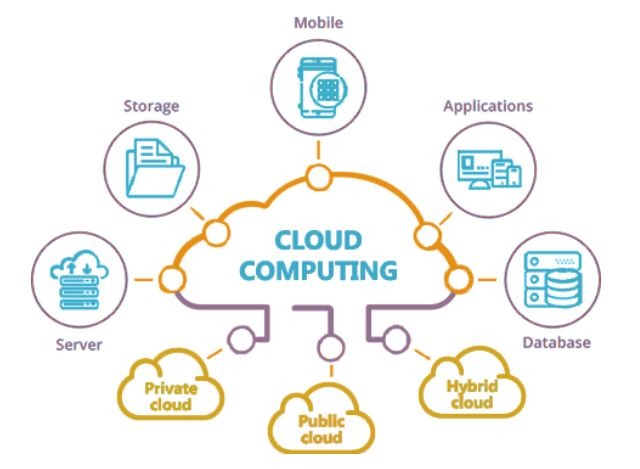
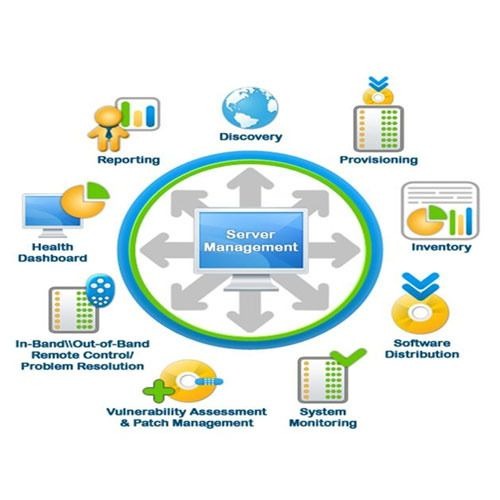
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)
Benefits and challenges of cloud adoption.Infrastructure as a Service (IaaS).Amazon Web Services (AWS)

Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs
Common threats: malware, phishing, DDoS, ransomware.Malware: viruses, worms, trojans, spyware. Firewalls, IDS/IPS, VPNs

Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data
Types of disasters: natural, technical, human error, cyberattacks.Risk assessment and business impact analysis (BIA) .Identifying critical systems and data

Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)
Linux distributions overview (Ubuntu, CentOS, Debian, Red Hat).Installing Linux in a virtual or physical environment. Basic commands (ls, cd, cp, mv, rm, etc.)

Perfect for beginners, offering essential courses and community support.
Great for advancing skills with diverse courses and added resources.
Unlimited access with expert mentorship and exclusive perks.

Courses Available
Active Learners
Expert Instructors
Awards Received






Global partners has been Publish the course you want, in the way you want always have of control.
9,500+ businesses & students around the world








Discover the must-have books of the season, from thrilling mysteries to inspiring biographies.
Discover the must-have books of the season, inspiring biographies.
Books of the season, from thrilling mysteries to inspiring biographies.